By KDnuggets -
2021-01-04
By KDnuggets -
2021-01-04
If you are just starting down a path toward a career in Data Science, or you are already a seasoned practitioner, then keeping active to advance your experience through side projects is invaluable to ...
 By techxplore -
2021-01-28
By techxplore -
2021-01-28
MIT researchers have developed a type of neural network that learns on the job, not just during its training phase. These flexible algorithms, dubbed "liquid" networks, change their underlying equatio ...
 By diginomica -
2020-09-24
By diginomica -
2020-09-24
How do you work backwards from thousands of disconnected PDFs to the 100,000 suspicious financial transactions they’re reporting on? A combination of hard human work, OCR, data analysis and graph.
 By Neo4j Graph Database Platform -
2015-12-23
By Neo4j Graph Database Platform -
2015-12-23
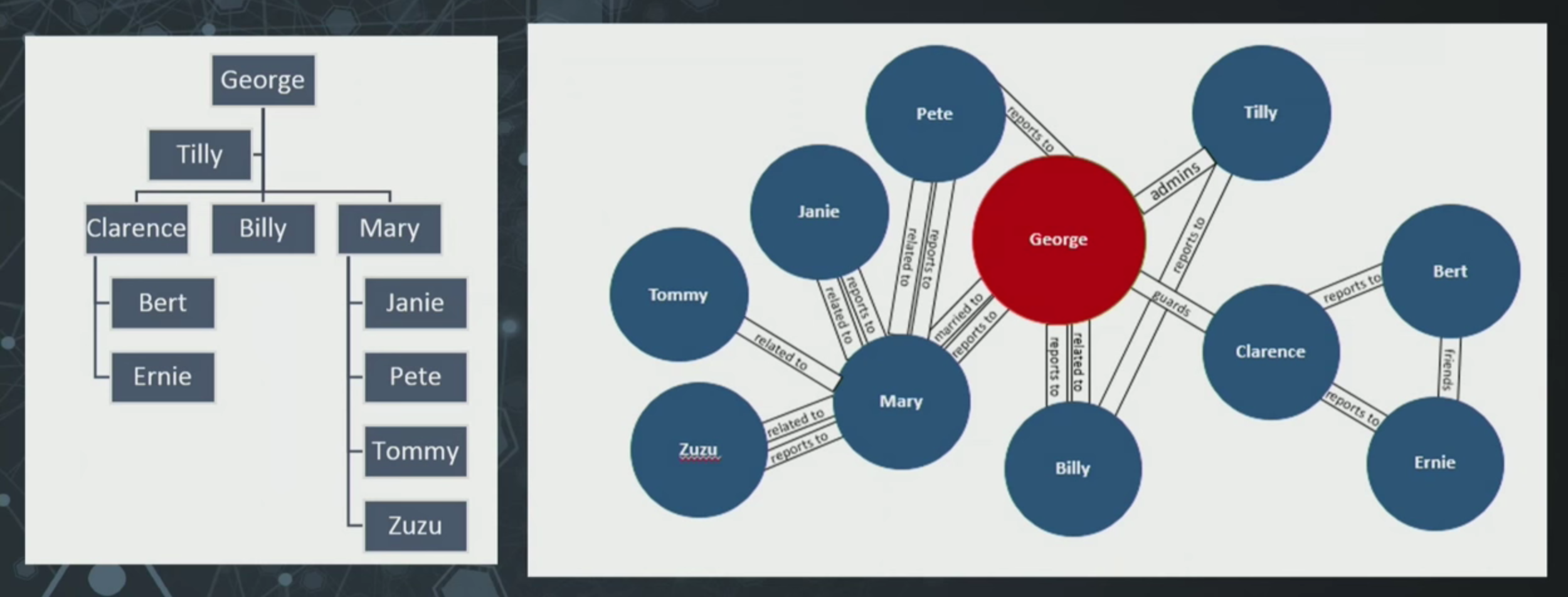
Watch (or read) Senior Project Manager Karen Lopez’s GraphConnect presentation on the signs that your data is actually a graph and needs a graph database.
 By Neo4j Graph Database Platform -
2020-08-17
By Neo4j Graph Database Platform -
2020-08-17
Read the second blog in Neo4j's new six-part series on how Neo4j's graph technology can help you combat money laundering.
 By datasciencecentral -
2020-11-24
By datasciencecentral -
2020-11-24
Abstract – Big data helps to make strategy for future and understand user behaviors. In 1959, Arther Samuel gave very simple definition of Machine Learning as…